Techtweek Infotech LLC, recognized as the Top cybersecurity company in India, partners with you to revolutionize cybersecurity, bolstering your business. Our transformative solutions fortify assets, propel growth, and instill confidence in a secure digital landscape, driving success.
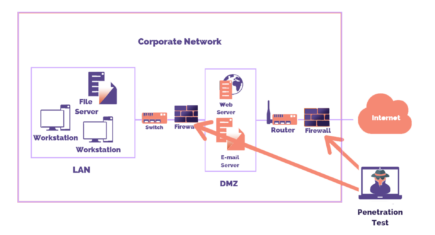
External Pentesting is a critical component of cyber security operations. Ethical hackers simulate real-world attacks from outside a company’s network to identify vulnerabilities in external-facing systems. By doing so, organizations can strengthen their security defenses, safeguard against data breaches, and prevent unauthorized access attempts.

Internal Pentesting includes authorized examination of an organization’s internal network, systems, and apps to spot vulnerabilities. Ethical hackers mimic real-world attacks from within the network to address weaknesses and boost cybersecurity, ensuring strong protection against potential threats.
Our Cyber Security service conducts thorough wireless penetration tests to assess the robustness of security measures preventing unauthorized access. By exploiting wireless vulnerabilities, we identify and address risks such as unauthorized access to private SSIDs or privilege escalation on guest SSIDs, ensuring the integrity of your network defenses.
Mobile devices and software are essential, simplifying and enhancing our daily lives. Hackers often target them due to the data they handle. From banking to healthcare, organizations use mobile apps creatively. Managing security risks is challenging due to daily vulnerability discoveries. As a leading cyber security company in India, we specialize in Mobile Application Pentesting, ensuring robust protection for your mobile apps against evolving threats.

A Web application (Web app) is a program stored on a remote server, accessible over the Internet through a browser. Web services, handling sensitive data like user and financial information, are often cybercriminal targets. As web apps grow in complexity, the number of exploitable vulnerabilities is increasing over time. With increasing complexity, a Security Operations Center (SOC) is vital to mitigate rising exploitable vulnerabilities in web apps.
Wireless penetration tests evaluate the effectiveness of security controls guarding against unauthorized wireless access. These tests aim to exploit wireless vulnerabilities, gaining access to private SSIDs or elevating privileges on guest SSIDs meant to be isolated from private networks.
Our Cyber Security Experts can tailor a security solution for your business to ensure that your system is safe from any threats, attackers, or any kinds of vulnerabilities.
With a strong team of Cyber Security Specialists, develops a robust access management system and operates a Security Operations Center to ensure secure business data.
We offers Cyber Security Specialists for hire to establish a user-identity and control management system, along with other cybersecurity solutions, ensuring complete security for your business.
Enhance your system’s defenses with tailored cyber security services, receiving custom configurations that align with your business requirements, address security needs, and guarantee comprehensive protection.
“Techtweek Infotech’s cybersecurity services have been instrumental in safeguarding our business from potential threats. Their expert guidance and support have helped us develop a robust security posture and maintain it over time.”
“We engaged Techtweek Infotech for network and web application penetration testing, and their team provided invaluable insights into our security vulnerabilities. Their recommendations have significantly improved our overall security.”
“Working with Techtweek Infotech has been an exceptional experience. Their cybersecurity consulting services and penetration testing have helped us address critical security gaps and strengthen our defences against potential attacks.”
We provide our cybersecurity services and penetration testing to businesses across various industries, including finance, healthcare, retail, technology, and more.
How often should penetration testing be performed?The recommended frequency for penetration testing is contingent upon your organization’s risk assessment and regulatory obligations. Generally, it’s suggested to carry out penetration testing at least once a year or whenever substantial modifications are made to your infrastructure.
Can you help with compliance-related cybersecurity assessments?Yes, our team can assist with compliance-related cybersecurity assessments, such as PCI DSS, HIPAA, GDPR, and more, ensuring your organization meets regulatory requirements.
What is the difference between vulnerability assessments and penetration testing?Vulnerability assessments focus on identifying potential weaknesses in your systems and infrastructure, while penetration testing actively exploits those vulnerabilities to assess their impact and severity.
How do you ensure the confidentiality of my business information during penetration testing?We maintain strict confidentiality and follow industry best practices to safeguard your sensitive information. We also sign non-disclosure agreements (NDAs) to ensure the protection of your business data.
In the realm of cybersecurity, we uphold rigorous confidentiality standards and adhere to industry-leading practices to protect your sensitive information. Additionally, we take the extra step of signing non-disclosure agreements (NDAs) to guarantee the utmost safeguarding of your business data.